Trainings & CTFs
Learning security through labs and workshops
Building security into your project from the beginning.
An ounce of prevention is worth a pound of cure. Pentesting is meant to catch issues at the end of the development lifecycle. If you build security into the design of your project from the get-go, it’s not only cheaper to implement security fixes compared to finding them after the fact, but there’s also more clarity. When you understand the system being built from a security perspective, evaluating and prioritizing different security features becomes much easier.
If you need help evaluating security concerns earlier in the project, Lightfoot Labs can help you with consulting throughout the development lifecycle.
Threat modeling is a systematic way of evaluating security concerns within a product or system. If you don’t know what the attack vectors are, you cannot prioritize mitigations.
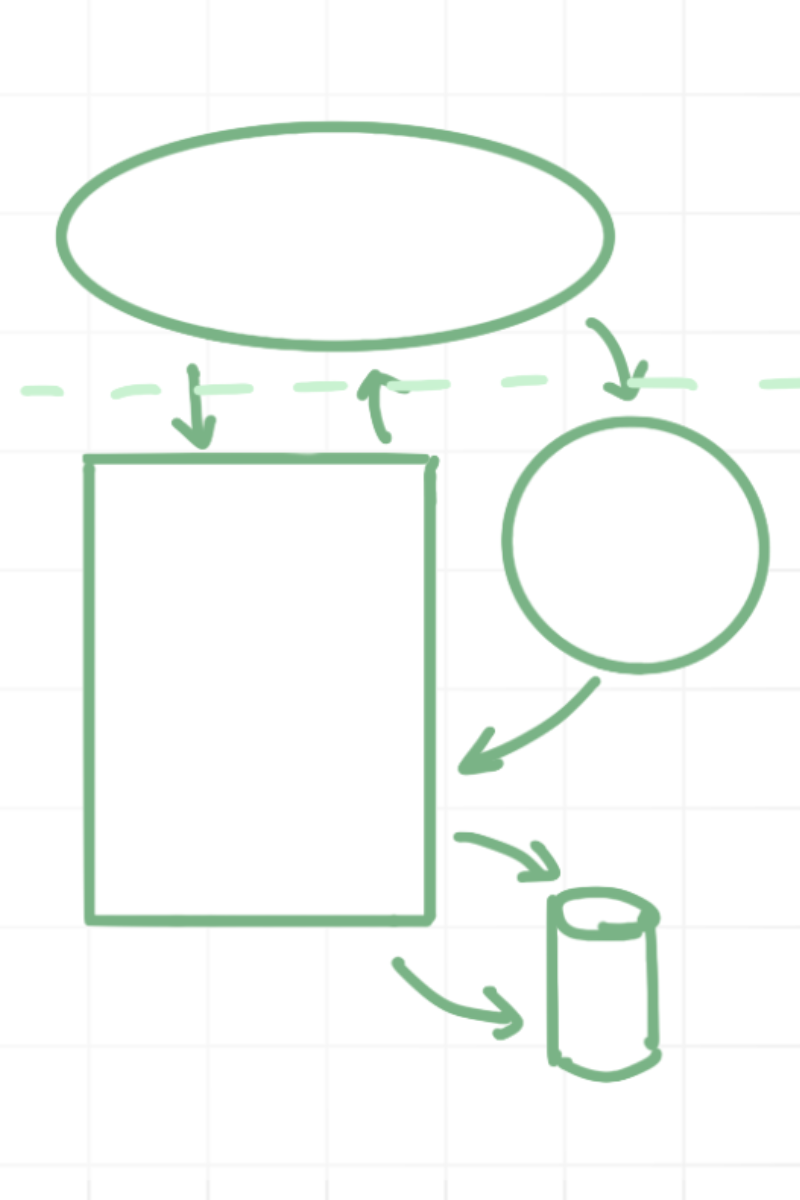
Here’s how it works: all of the components of a system are identified, as well as connections between different parts. Assets–important pieces of data, access, or other information that need to be protect–are mapped to this model, and likely threat actors are identified.
This information is then used to thoroughly enumerate all attack methods relevant to the system being described. That means that threat models are unique to the system under test. These attack methods can be ranked based on likelihood of execution (difficulty and insider knowledge needed) ad as well as the damage they would cause. This allows engineering and design teams to then:
This allows you to proactively identify and tackle security concerns before pentesting or certification.
If you need help building secure design into a project, you have a range of options from a one-off discussion to an in-depth threat model to ongoing project support. Technical decisions often require having a threat model to understand the system so that any recommendations are a good fit for the project and for overall company concerns.
In the past, I have done threat modeling, TARAs, presentations on design concerns, written guides for engineering teams to implement security features on their specific hardware, and more.
Reach out to discuss how I can help you secure your projects.